Service hotline
+86 0755-83975897
Release date:2022-06-16Author source:KinghelmViews:2829
/ Introduction /
In news conference of main engine plants, take functions relating to internet of vehicles as unique selling points still accounts for half of the market, such as remote control of air conditioner, remote seat heating, remote update. Automobile starts to have interaction and serve capabilities, and evolve from simple transportation vehicle to super intelligent terminal connecting all things via connecting vehicle with internet and carrying various intelligent hardware such as sensors, controllers, actuator,etc..
Internet of things revitalize s automobile, and make the relative closed automobile be exposed to open internet environment that may suffer from threats of network information security. The system of internet of vehicles includes personal information, frequent contacts, usual address and other sensitive information of the owner. Once these information are stolen illegally, it may lead to privacy disclosure and possess loss to infringe personal safety.
The typical event causing by problems of automobile information security happened on FIAT Chrysler Automobiles company in 2015. In a information security test, many experts in information security use the network channels of entertainment host and external physical interfaces removed from automobiles of FCA to invaded cloud of FCA and forged and sent remote control orders to vehicles, ending with successfully operating modules such as air conditioners, instruments and windshield wipers. Those attacks may happen when automobiles are not started or in driving with enormous security risks. Subsequently, FCA announced to recall 1.4 million automobiles and trunks with information security risk.
Information security risks met by automobiles in open environment mainly come from vehicle terminal, cloud service platform, communication link and external ecology and other aspects. Main engine plants have attached more and more importance to information security of internet of vehicles after going through barbaric growth of internet of vehicles, and improve protective capability of information security of automobile via various methods, including enhancing graded and classified management and access control of internet of vehicles in all life circle; improving identity authentication system in processes of vehicle development, production and usage; establishing multi-lateral cooperative, information-sharing and real-time and precise security service platform.
As the supervisors, relevant national authorities has gradually established and improved security management system (national standard, industry standards) relating to internet connected automobiles to strength risk prevention and control and security prevention capabilities for information security.
This is the fifth volume of malicious words for the circle of internet of vehicles, which analyzes typical automobile cloud architecture in internet of vehicles and potential risks of information security, and introduces some universal schemes for information security.

Overall Automobile Cloud Architecture in Internet of Vehicles
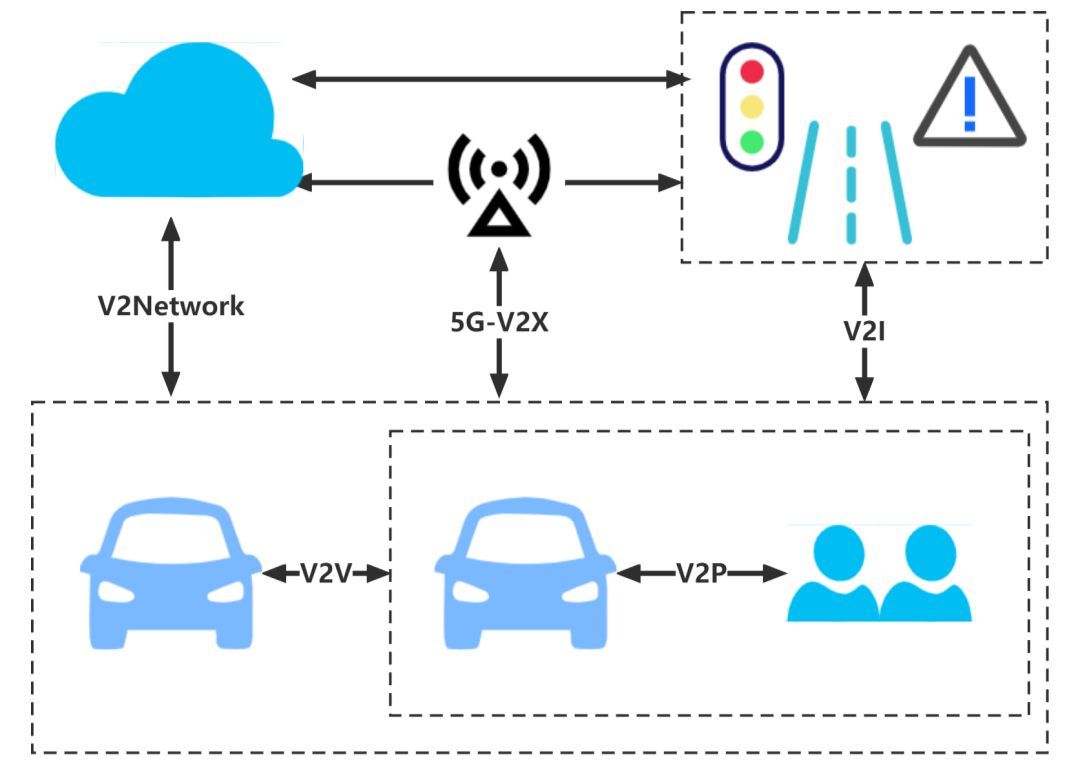
Frequent architecture in internet of vehicles is cloud-link-terminal architecture. In particular, cloud refers to cloud service platform, terminal refers to vehicle terminal, and link refers to communication link connecting cloud service platform and vehicle terminal. Hence, general cloud-link-terminal architecture scheme is shown in the following figure.
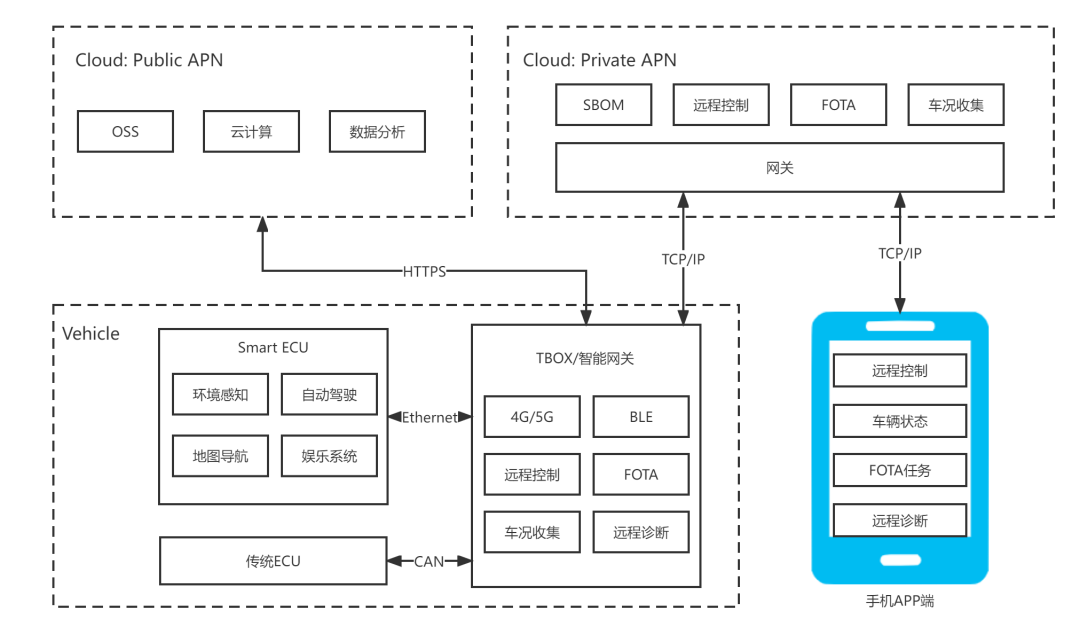
Normally, there are two APN (Access Point Name) in cloud service platform, one is responsible for accessing public domain and the other is responsible for connecting private domain. In particular, public domain is in charge of application with high requirements for storage resource and computing capability such as file store and cloud computing. Private domain is in charge of businesses such as communication and exchange of vehicle sensitive data, vehicle control and FOTA, which is the main lifeline of internet of vehicles of main engine plants and is capable of running authentication and routing services to vehicle terminals accessing vehicles.
Vehicle terminal is mainly TBOX/ intelligent gateway with built-in 4G/5G communication module. Communicate with outside via remote communication technology and cloud service platform, and communicate with inside via CAN/LIN/vehicle Ethernet and other internal ECU to provide the collection of operating data, remote inquiry, control, diagnosis and update and other services.
In terms of communication link connecting cloud service platform and vehicle terminal, public domain and vehicle terminal generally adopt HTTPS Protocol, and private domain and vehicle terminal generally adopt TCP/IP Protocol, while internet application level for scenes with many accessing vehicles/equipment adopts MATT Protocol.
As other systems involving cloud and equipment terminals, risks of information security for cloud-link-terminal architecture in internet of vehicles mainly include: fixed cloud, monitor of communication link, disclosure of key for vehicle, communication security of local network, etc..
Strategic Analysis of Cloud Threats
I. Severer Security
Cloud service platform in automobile field is similar to that of traditional internet field, which is vulnerable to suffer risks of severer being invaded, causing disclosure of sensitive data and fixed key orders that damage the rights and benefits of the owners.
All main engine plants generally guarantee information security via means of “locking” sensitive data and important services. Block access of illegal users via measures such as private wire network, identity authentication, setting independent room for professional operation and maintaining.
II. Service Interface Security
Frameworks represented by SpringCloud are generally applied as development foundation to build cloud service platform lately for advantages of micro-services architecture such as deployment flexibility and elastic expansion. Some of internet of vehicles business in main engine plants need to obtain data relating to users, vehicles and parts, and take these data as the basis of work flow. Data sharing and communication among multiple platforms and systems are generally achieved by Web Service interface of micro-services architecture.
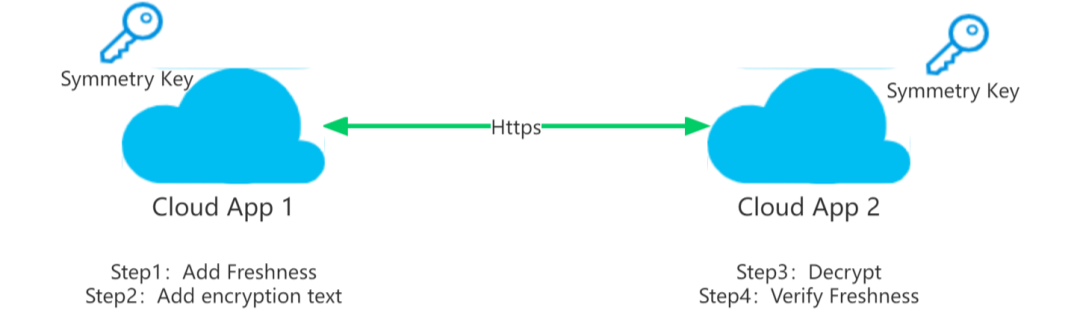
To verify the identify of sender and insure data integrity, data transmission interface generally adopts HTTPS Protocol to guarantee the authenticity of sender’ identity. Meanwhile, verify data integrity by regularly changing symmetric key, encrypting message, adding MAC verify field or other means. Main engine plants also are able to manage freshness by means such as adding freshness fields (such as timestamp) in message to prevent replay attacks from attackers using the same data.

Threats Analysis and Strategy of Communication Link
There are multiple communication links in cloud-link-terminal architecture including communication link for cloud service platform and base station, communication link for base station and vehicle terminal, communication link for phone and base, etc..
Public domain of internet of vehicles, being mainly responsible for businesses such as upload/download and cloud store of non-sensitive documents or log of vehicle terminal, adopts HTTPS Protocol to meet needs of information security. Private domain is responsible for business such as arranging interactions among sensitive data, thus the communication terminal of private domain shall be able to handle higher-lever threats of information security, which include forging vehicle terminal, illegally connecting cloud service platform; phishing cloud service platform; sensitive information disclosure because plaintext transmission of orders or business data is intercepted and captured; security accidents because orders or business data are intercepted and tampered; etc..
Attackers can hijack session to steal intellectual property or sensitive data of vehicles via means including forging base station and DNS hijacking in attacking communication link. For instance, monitoring and stealing upgrade package and reverse engineering ECU firmware in FOTA business.
Attackers can distort cloud communication links via physical interface of vehicle, and attack vehicles via forged server. For instance, carrying out endless data attacks to run out of storage space of controller of vehicle terminal that fails to operate regular businesses. Or, copying TBOX software to other device pretending it as the illegal access to cloud service platform from legal vehicles.
It is urgent that high-strength identification shall be given to core entity objects (cloud service platform, vehicle terminal, etc.) in business of internet of vehicles to insure uniqueness of entity objects, and high-strength bidirectional identify verification that vehicle terminal accesses cloud service platform shall also be realized basing on identifications of all entity objects through analyzing above risks and combining business processes of internet of vehicles and frequent interactions between vehicle and cloud.
Public Key Infrastructure (PKI) is a general and standardized key management platform, providing information security service via adopting asymmetrical encryption algorithm technology, which can transparently provide key and certificate managements to all network applications required by cryptogram services such as encryption and digital signature. In the application of Internet of Vehicles, PKI can provide credible description of identification to various entity objects, and sign and issue unified digital identification-digital certificate to objects to build a creditable networked virtual environment. It provides base support to guarantee confidentiality, completeness and non-repudiation of information.
Logic relationships among subsystems of PKI are shown in following figure.
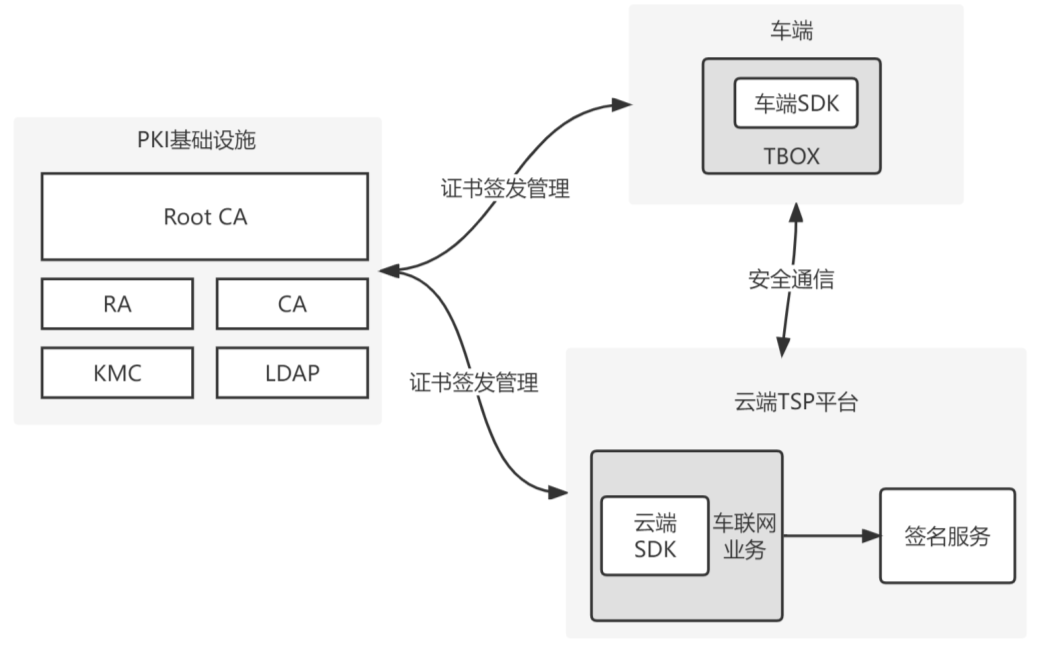
Cloud devices accessing network and vehicle terminals need certificate signed and issued by PKI. The activation towards controller such as TBOX, AVN is certificate signing and issuing in PKI, and processes of this is elaborated as follows:
Step 1:TBOX produces public and private keys and applies for formulating P10 (P10 includes certificate subject, validity period and signature of above information), then sends the application to cloud;
Step 2:Cloud certificate management service verifies uploaded information and encapsulates P10 and other vehicle information as certificate application recognized by PKI, then PKI signs and issues certificate;
Step 3: Cloud sends the signed and issued PKI certificate to TBOX storage of vehicle terminal.
After activating cloud and device terminals (issue of certificate), communication entity can communicate with cloud basing on digital certificate.

Threats Analysis and Strategy of Vehicle Terminal
Automobile generally adopts CAN bus to connect other ECU or sensor devices in automobile. Attackers can hijack any nodes via its broadcast mechanism and send message to other nodes in bus after obtaining control of bus, because CAN bus communication lacks of authentication capability and encrypted communication function. Therefore, CAN bus is confronted with risks of various attacks, including replay attack, flooding attack, discarding attack, etc..
Hardware Security Module (HSM), is base support for security scheme of vehicle terminal, and two information security strategies (TrustZone/TEE Execution Environment and SecOC Protocol) are realized basing on HSM, which will be introduced in following text. HSM writes information including algorithm, keys, encryption mode in hardware module cannot be tampered with, and deals with tasks relating to security including safe vehicular communication, operational detection in running, safe startup, refresh, log record and debugging to prevent attackers from obtaining access of vehicle internet via bypassing ECU interface relating to security.
I. Trustzone/TEE Execution Environment
TrustZone is security architecture of RPM A-profile architecture. TrustZone divides CPU into two working conditions that are NWS (Normal World Status) and (Secure World Status). Chips enabling TrustZone provide hardware-level protection and security isolation to outer hardware resources. No application can access security hardware device, internal storage and caches of SWS and other outer security hardware device, in which there is system-level hardware quarantine enforcement.
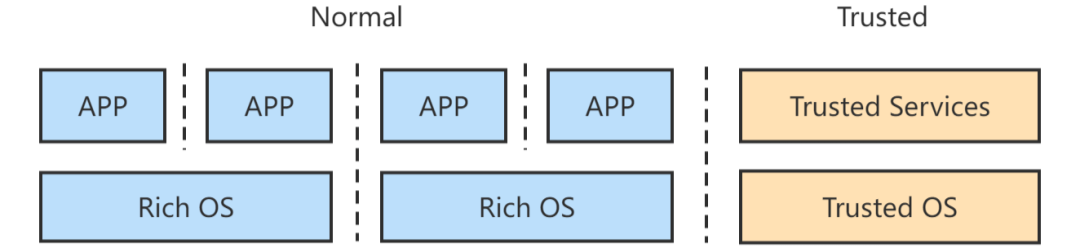
Operating system and application run in NWS, while TEE runs in SWS. Generally, one TEE includes multiple trust servers hosted by lightweight kernel, providing services including key management and relevant API to developers.
A complete SoC consists of ARM kernel, system bus, RAM on chip and other outer components. Controller for ARM kernel shall support TrustZone and cooperate with other components to realize hardware-level protection and quarantine measures for chips. Following figure is a hardware structure of SoC supporting TrustZone.
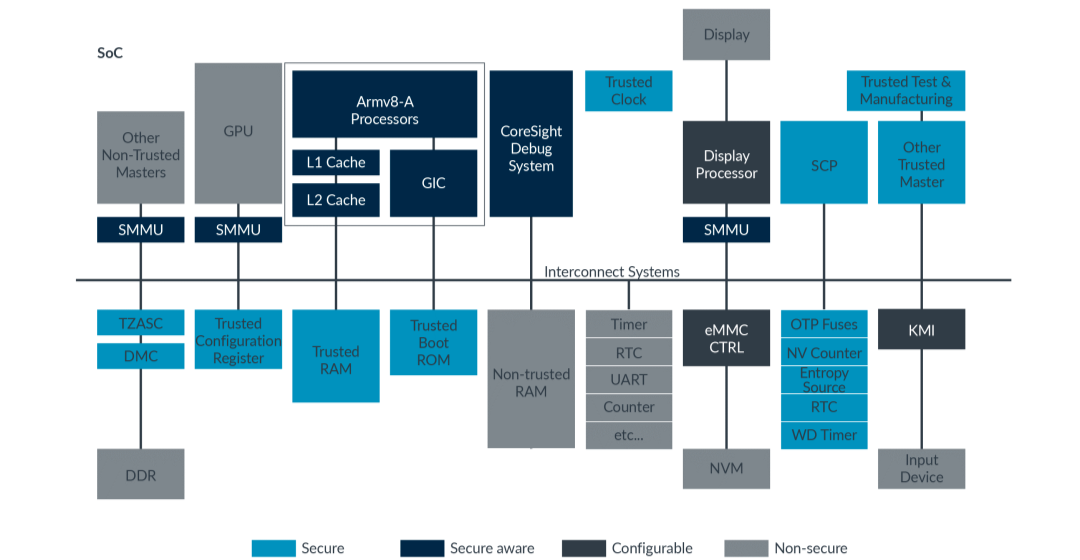
The hardware isolation function of TrustZone for external resources and memory resources can improve security level of system. Hardware isolation includes interrupted isolation, RAM and ROM isolation on chip, RAM and ROM isolation off chip, hardware isolation of outer devices, outer RAM and ROM isolation, etc..
To realized various isolation at hardware level, corresponding expansion towards hardware and CPU core of the whole system shall be conducted, including virtualization of CPU core, dividing operating state into NWS and SWS; adding read/write signal wire of security bit on bus; adding security bit of Memory Management Unit (MMU) page table; adding security bit for cache; other outer components providing control and signal of security operation; etc..
II. SecOC Protocol
Recently, encryption communication of bus in vehicles has became a hot topic. To adhere to requirements of data encryption and verification, AUTOSAR institute added SecOC(Secure Onboard Communication)component, introducing a set of standards for communication encryption and verification, which was an effective information security scheme on in-vehicle network.
SecOC is an information security component in software package of AUTOSAR, which adds a series of functions and new requirements including encryption/decryption algorithms, key management, freshness management and distribution. SecOC can provide available and feasible identify verification mechanism to message data of CAN/CANFD bus, which integrates well with current ARA communication mechanism of AUTOSAR with small consumption. It is based on MAC identification of symmetric algorithm, which can insure security at the same level of non-symmetric algorithm with shorter secret key.
Transmission and reception controllers shall integrate SecOC module in case of communication controllers need to realize SecOC Protocol. Original message is named as Authentic I-PDU, SecOC module obtains MAC value via conventional algorithm basing on original secret data and keys. Secured I-PDU will emerge after integrating message header, original message, freshness and MAC, and the structure is shown in following figure.
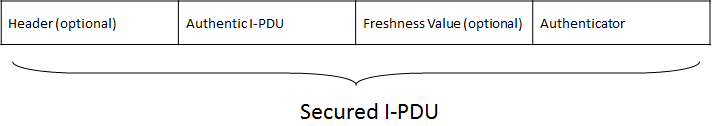
SecOC is mainly based on two means to insure verification of authenticity and completeness of data, which are identify verification basing on MAC and preventing reply attack basing on freshness. Firstly, MAC is one of cryptography methods insure data completeness and verification, the function of MAC message identification code in SecOC Protocol is verifying authenticity of message data. However, additional security measures are required to insure confidentiality of message.
Secondly, freshness value shall be added in Secured I-PDU to reduce risks of replay attack. Freshness value is a value that upgrades in accordance with a certain logic. AUTOSAR recommended counter may create new freshness value basing on timestamps. Two key sections shall be defined and completed in implementation of SecOC scheme by OEM: freshness value management and key management. Communication encryption and verifying processes are shown in following figure.
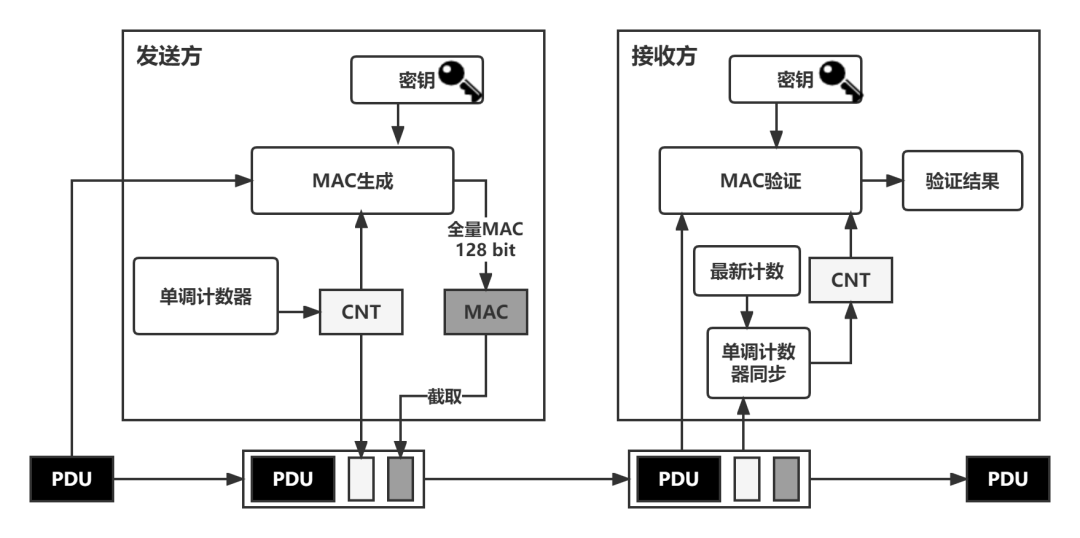
SecOC module sending nodes generates freshness and MAC, then consists of Secured I-PDU with original message, and broadcast via CAN bus.
SecOC module receiving nodes verdicts source and completeness of original message via verifying MAC. Freshness value verifies whether this message is repetitive and legal or not.

Conclusion
Automobile faces more and more serious threats in information security with improvement of technologies of Internet of Vehicles, automobile electronic architecture and in volume production of automatic drive. All main engine plants and Tier1 need to improve information security capability of each internet of vehicle platform through establishing security protection system, continuous risk analysis and optimization of attacking and protection strategy.
(This article is selected from Internet, suggestions and opinions do not represent position of us. In case of infringement, please contact us to delete!)










Copyright © Shenzhen Kinghelm Electronics Co., Ltd. all rights reservedYue ICP Bei No. 17113853